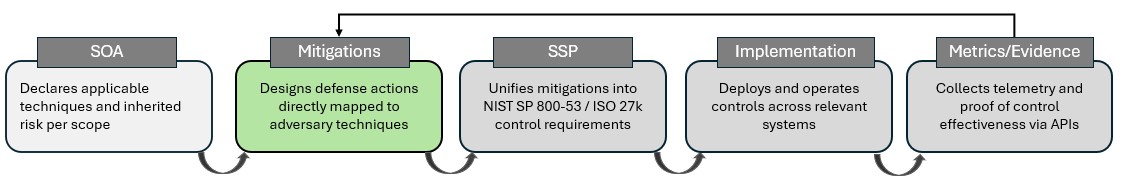
Cybersecurity leaders have long recognized that knowing exposures is not enough. Mapping adversary techniques to business processes provides the foundation for a defensible risk model, but resilience depends on what happens next. Traditional mitigation practices—manual registers, spreadsheet plans, static “to-do” lists—rarely keep pace with live adversary activity or with the changing priorities of the business. The result is an uncomfortable gap: risks are known but not acted upon in a timely, structured, or accountable way.
Attestor.ai closes this gap by transforming mapped exposures into automated, optimized, and continuously updated mitigation plans. Where traditional governance models produce static lists of controls, Attestor.ai generates System Security Plans (SSPs) that evolve as adversary behavior and business contexts change. This ensures that defenses are never frozen in time, but instead evolve dynamically in step with the threats they are designed to counter.
From each Statement of Applicability (SoA)—which declares applicable techniques and calculates inherited risk per scope—Attestor.ai generates a set of defense actions directly mapped to adversary techniques. These are not left as abstract prescriptions. Instead, Attestor.ai consolidates them into System Security Plans (SSPs) aligned with standards such as NIST SP 800-53, ISO/IEC 27001 Annex A, or the CIS Controls. SSPs provide a clear, auditable record of what mitigations are required, why they are required, and how they are tied to authoritative frameworks.
This automation removes the duplication and error of manual planning. More importantly, it ensures that every exposure surfaced through mapping has a defined mitigation path, leaving no gaps between intelligence and defense.
Unlike static registers that stop at “what should be done,” SSPs in Attestor.ai are operationalized. Mitigations are translated into concrete control implementations, deployed across the relevant systems and environments. This closes the gap between planning and execution, ensuring that mitigation items result in real, enforceable defenses.
Every deployed control generates telemetry and proof of effectiveness, collected automatically through control APIs. These implementation metrics are not an afterthought; they are integral to the loop. Attestor.ai continuously feeds this evidence back into the mitigation design process, ensuring that defense plans are recalibrated based on how controls actually perform in practice.
The result is not just a plan that looks good on paper, but a living system where mitigation strategies evolve in lockstep with operational evidence.
Traditional approaches often default to simplistic rankings: protect the “crown jewels” first, patch the highest CVSS scores, or address the latest audit findings. While intuitive, this approach is blunt and often ineffective. High-value assets may be exposed to low-probability techniques, while less critical systems may face adversary behaviors that are highly active in the wild.
Attestor.ai replaces this bluntness with multi-dimensional optimization. Mitigation plans are calibrated across three lenses:
By balancing these factors, Attestor.ai doesn’t just rank mitigation items—it optimizes them. Scarce resources are applied where they most reduce adversary opportunity, while over-control in low-risk areas is avoided.
What truly differentiates Attestor.ai is not only the creation of mitigation plans, but their continuous adjustment. Every time a scope’s attributes change, intelligence reveals new adversary tradecraft, or MITRE ATT&CK techniques are updated, the associated mitigation plans are recalibrated.
Each change is versioned and traceable, creating a defensible chain of reasoning: this technique was added because intelligence shifted; this mitigation was adjusted because business exposure increased. For CISOs, this ensures no mitigation plan is stale; for auditors and regulators, it offers a transparent lineage from exposure to defense.
The cumulative effect is a model of continuous improvement. Where traditional mitigation registers quickly grow obsolete, Attestor.ai ensures mitigation plans evolve in lockstep with both the organization and the threat landscape. Defenses remain current, right-sized, and accountable—actionable for security teams, auditable for regulators, and enforceable at the business level.
Instead of a cycle of static checklists punctuated by fire drills, organizations gain a disciplined, dynamic loop of defense. Each change in adversary behavior or business scope flows naturally into updated plans, which are implemented, measured, and refined based on live telemetry.
This is how cybersecurity becomes not just a compliance exercise, but a living system of governance and improvement.
This article has focused on how Attestor.ai designs, optimizes, implements, and maintains mitigation plans in alignment with adversary behavior and business needs. The next article will extend this into AI-driven cyber risk management: how residual risk is recalculated in real time, how evidence is continuously validated, and how boards and regulators gain transparent, traceable assurance from the same reasoning model.